azure backup restore protected files
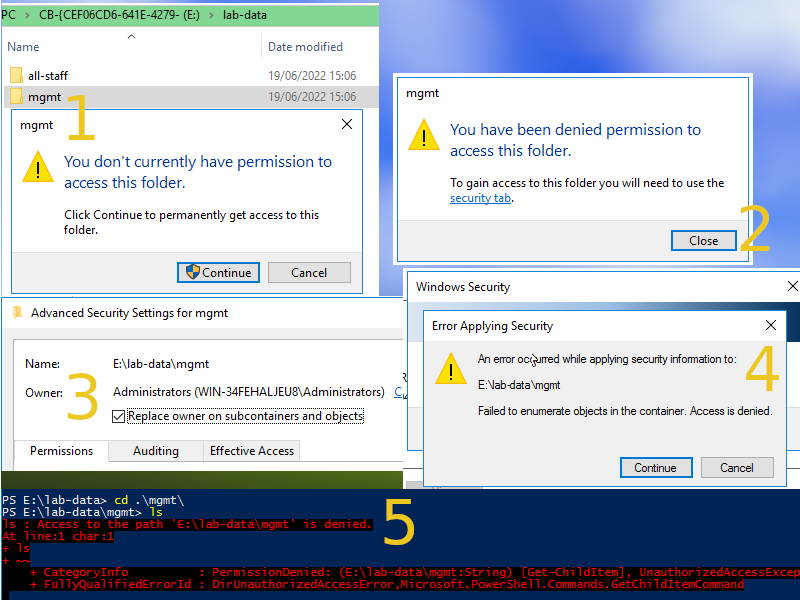
Restoring select files and folders from Azure backup is a straight forward process, a disk is mounted in the OS you're restoring to and you can just browse and copy/ paste what you want out. There can be permissions issues however that add some complications to this. Two examples that spring to mind are:
- You have a folder with very restricted access (think management or CEO) and by design Domain Admins do not have access.
- You've setup redirected folders using Microsoft's recommended configuration which by design, has restrictive permissions.
There should be no issue with the above, the backup runs under System so the files get backed up however the way Azure backup does selective files/ folder restores adds complications. The mount is read only (so you can't change ownership) and the permissions persist in the mount (so your admin ac won't have access).
Below are two methods to get access to the files. Both are less than ideal but I've not been able to figure a cleaner method (yet!). Both methods make use of the invaluable Sysinternals PsExec
The Problem: No amount of attempted permissions or ownership changes will apply to the read-only mount
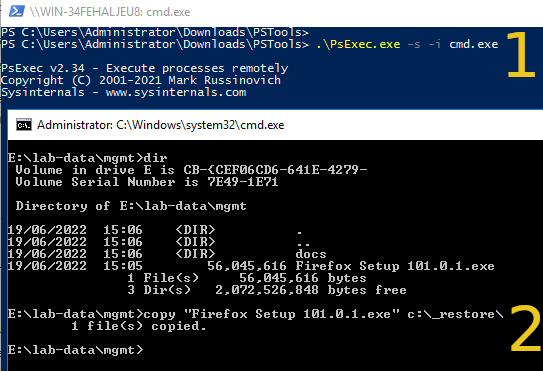
Method 1: Use PsExec to launch a command shell as System
- Launch an elevated PS or CMD shell
- Run the following
PsExec.exe -s -i cmd.exe - The new shell is running as System so you can traverse into the restricted folders
- Copy out what you need (copy to an accessible location, not "Desktop" as it will be the System's Desktop)
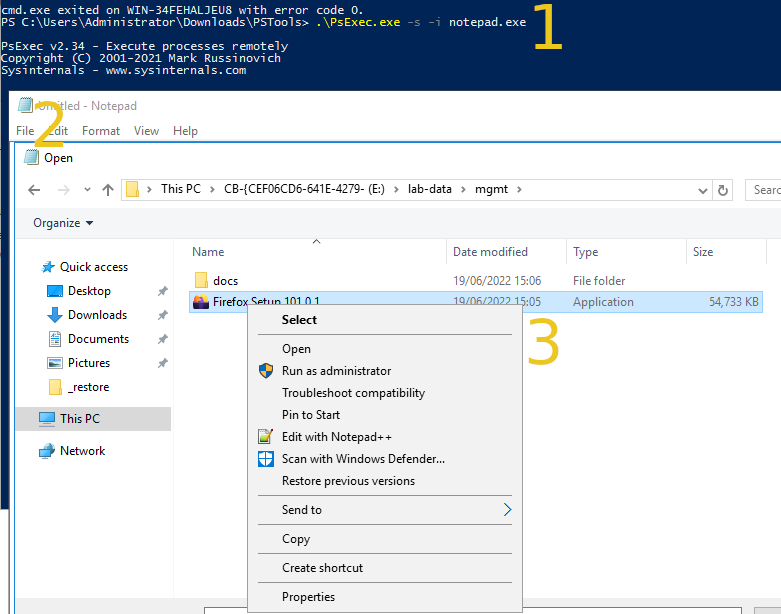
Method 2: Use PsExec to launch notepad as System; use the File->Open menu as a GUI for your restore
- Launch an elevated PS or CMD shell
- Run the following
PsExec.exe -s -i notepad.exe - Notepad is running as System, use the File-Open menu to traverse the restricted folders.
- Within the File-Open menu, copy out what you need (copy to an accessible location, not "Desktop" as it will be the System's Desktop)
- Note: I tried multiple ways of launching explorer.exe as System but it never gave me an interactive shell, this is by design to prevent it being hijacked.