security onion explore pcap
I recently took some blue team challenges at Blueteamlabs and a few of them involved analysing a .pcap file to pick some info out and determine what sort of an attack took place and answer a few questions. The first of these was relatively straight forward as the .pcap file was pretty concentrated around the attack so viewing in WireShark it wasn't too difficult to spot the attack and extract the relevant info.
While doing the challenge and scrolling (and scrolling...) through WireShark I wondered what the experience would be like using a more purpose built tool. I'd played around with Security Onion before so spun up a VM (more detailed post on that to follow sometime) to see how the next challenge would go.
- First need to scp the .pcap file over to security onion.
- Now we need to import it
sudo so-import-pcap ./traffic-with-dridex-infection.pcap - Once the import completes it should give us a link directly to the time range of the import.
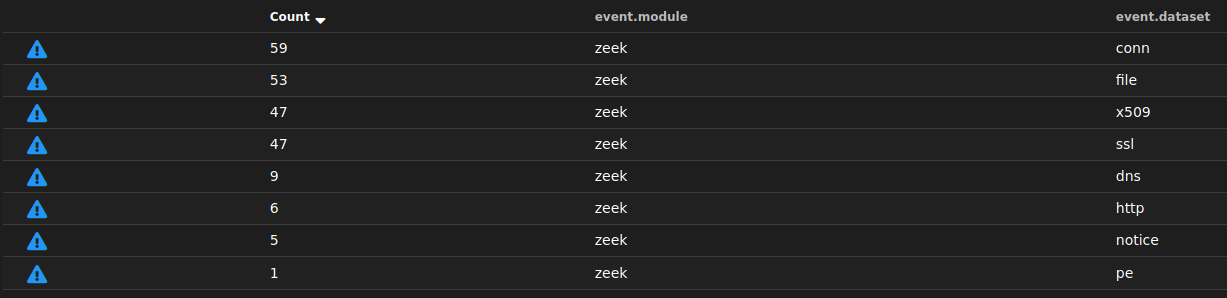
The initial view of the .pcap content immediately looks much more focused and straight away I was able to see likely source IPs and activity. The scope given for the task pointed to file downloads and it was very easy to locate the info given the top level data presented.
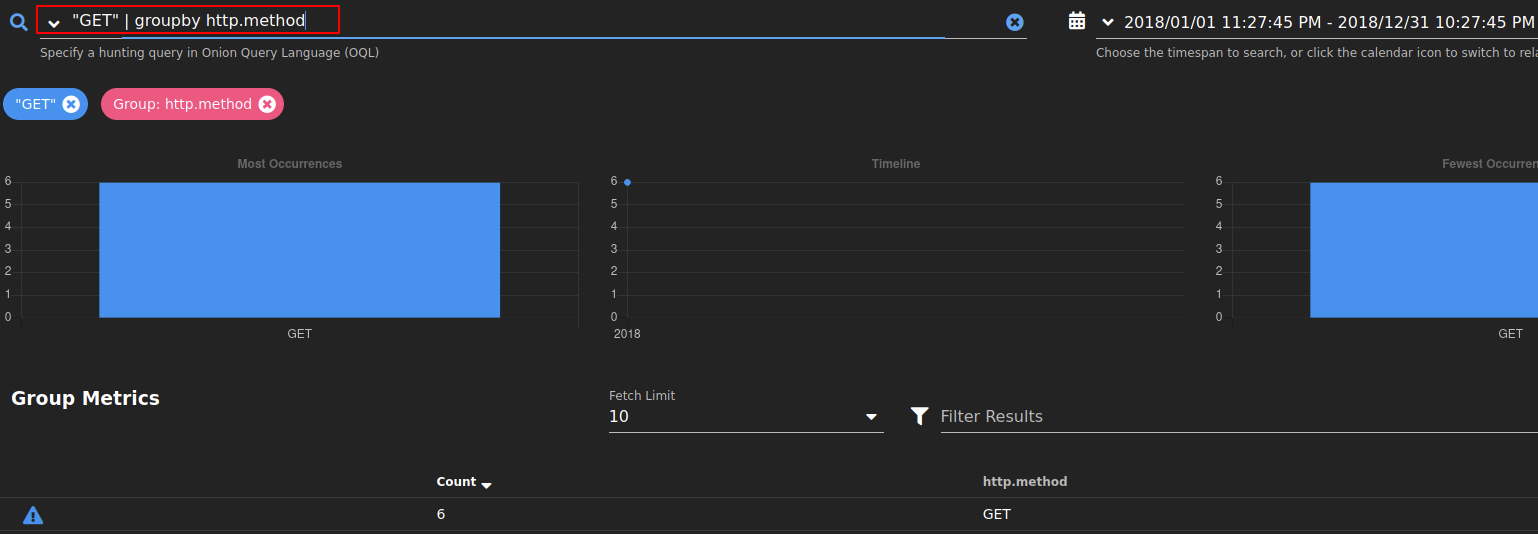
I spent a bit more time than needed browsing the data for the last couple of answers, that was more down to my lack of knowledge than anything else. Once I got the search syntax sorted the required info was front and centre.
Admittedly this was a fairly basic challenge and nothing I found using Security Onion could not have been found using WireShark for example, but it definitely brings the more relevant data to the front and I look forward to trying a more challenging ... challenge with it. Next step is to get some live data feeding into it too.
- note: I will expand this post once I get to go through a more detailed challenge