microsoft laps setup
I never got around to deploying Microsoft Local Administrator Password Solution (LAPS) in the previous domains I managed but it seems more and more like a tool I would want to deploy to help reduce lateral movement or domain wide exposure in an Ransomware situation. I'm going through the setup and config in a test environment to see what's what.
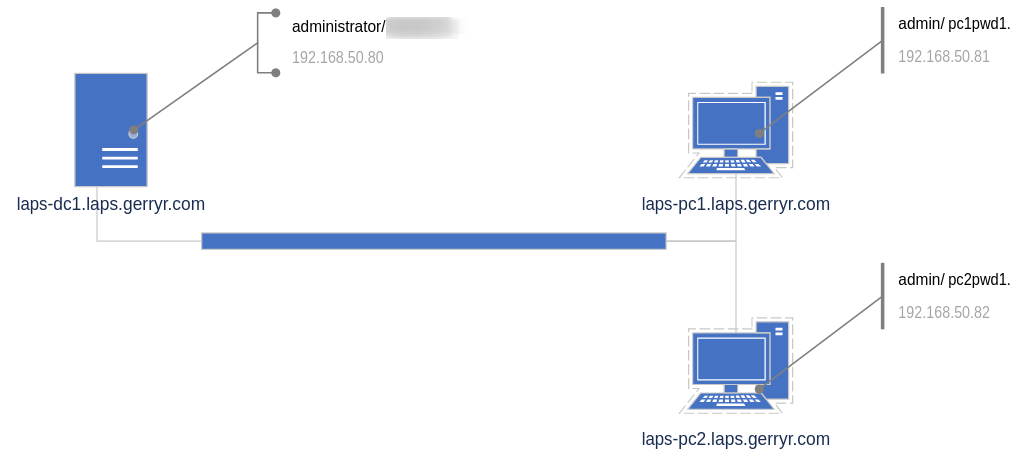
Network setup
First up was to setup a small environment, not best practice by any means but in this case I'll setup:
- 1 x DC (also use to manage LAPS)
- 2 x Windows Clients
Once this was setup and patched as per the diagram above I proceeded with downloading LAPS to the DC, taking a snapshot of the DC and beginning the setup. The setup consists of:
- Deploying LAPS client.
- Deploying management for LAPS.
- Configuring LAPS.
Deploying LAPS client.
There's a single msi (possibly more if you support a multi architecture environment) used for the Client and Management install. For simplicity sake we can setup a quick GP object to deploy the Client. Once created and linked to the computers OU the client installed after a reboot.
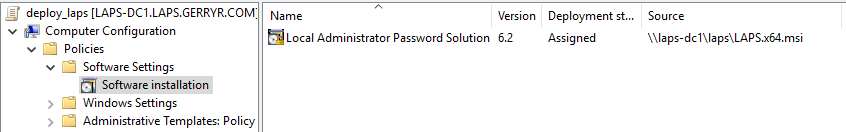
Deploying management for LAPS.
For the management component we want to install the opposite of the default install so we can manually run the .msi (LAPS.x64.msi) and deselect the Client component and select all the management components.
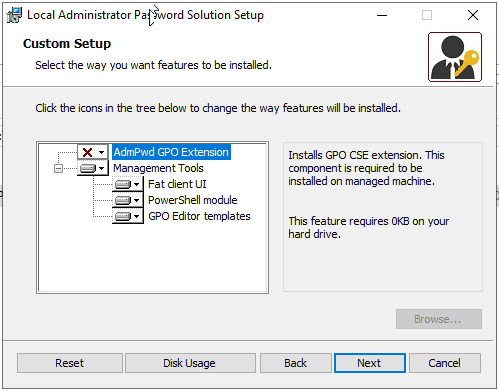
Now we need to prep our schema to support the new attributes. From an elevated PS prompt on our DC we run:
import-module AdmPwd.ps update-AdmPwdADSchema
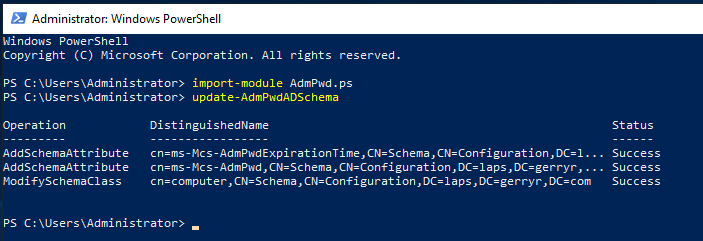
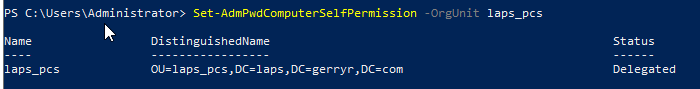
Next we need to make sure Computer objects have the required permission to update the new attributes for their respective object (repeat for all OUs you plan on managing with LAPS).
Set-AdmPwdComputerSelfPermission -OrgUnit laps_pcs
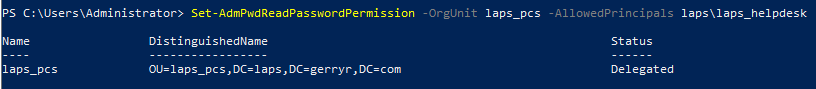
Optionally, if you have a specific user group that you want to allow access to view (1) and/ or reset (2) passwords that don't have domain admin rights (e.g. a helpdesk team) you can give that group the required access.
Set-AdmPwdReadPasswordPermission -OrgUnit laps_pcs -AllowedPrincipals laps\laps_helpdesk Set-AdmPwdResetPasswordPermission -OrgUnit laps_pcs -AllowedPrincipals laps\laps_helpdesk
Note you can use Find-AdmPwdExtendedRights -identity laps_pcs to see who currently has access.
Configuring LAPS.
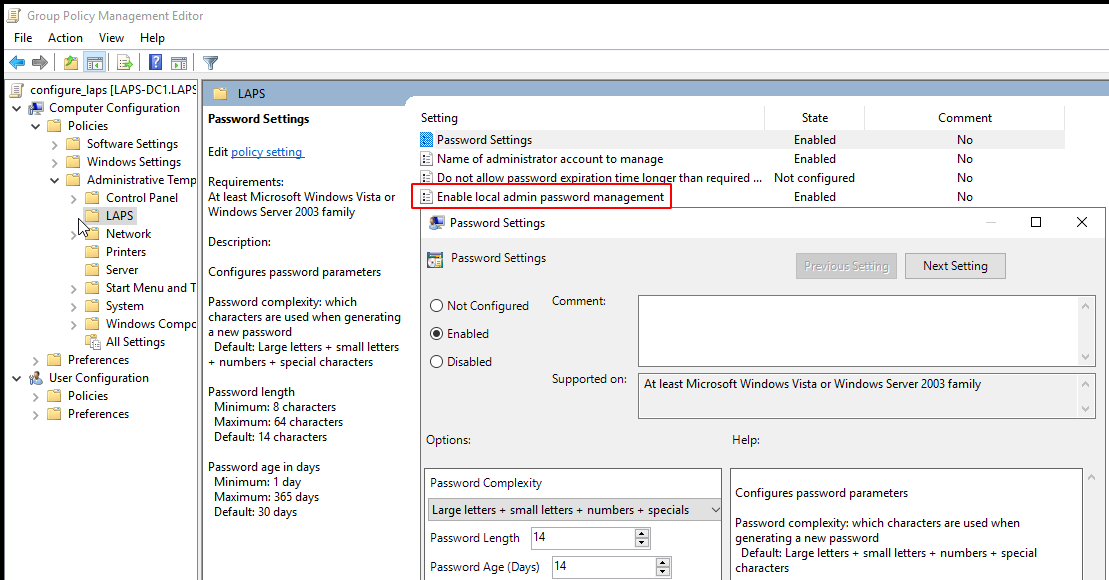
Configuration of LAPS is done through Group Policy so we can create another GP object and link it to our Computers OU:
- Configure the
Enable local admin password managementsetting to enable LAPS manage our local admin password, this is minimum setting change required. - In the screenshot below I also changed the
Password Settingsto reduce the max password age. - I also had to configure the
Name of administrator account to managesetting as I had setup a non standard local admin ac on the workstations.
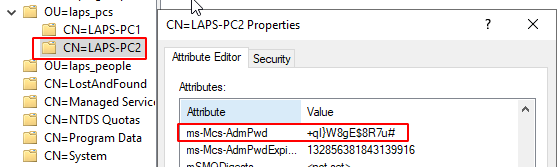
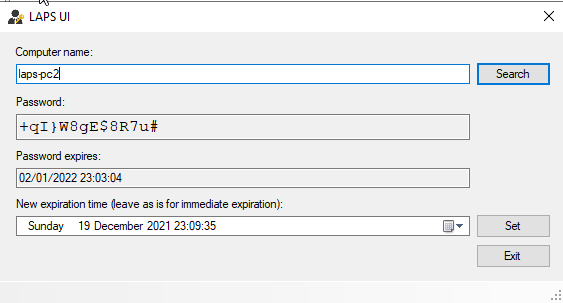
- Once the GP settings have kicked in we can now access the local admin password by checking the
ms-Mcs-AdmPwdproperty for a computer in ADSI Edit, or by using the LAPS UI we installed on the server earlier. - We can also reset the password in the GUI either for now or some time in the future, and once GP next syncs, the password reset will be implemented.
- Once applied, you can now use the local admin account with the unique auto-generated password when carrying out client changes that require admin rights. Now if one admin password is compromised it cannot be used to access other clients on the network.
Note you can also use the Reset-AdmPwdPassword -ComputerName pcname -WhenEffective date PowerShell command to issue a password reset.